About Us
GenCyber Program
The GenCyber Hawai‘i program provides yearlong cybersecurity camp experiences for students and teachers. The goals of the program are to help all students understand correct and safe on-line behavior, increase interest in cybersecurity and careers in the cybersecurity workforce of the Nation, and improve teaching methods for delivering cybersecurity content in K-12 computer science curricula.
Our vision is for the GenCyber program to be part of the solution to the shortfall of skilled cybersecurity professionals. Ensuring that enough young people are inspired to direct their talents in this area is critical to the future of our country's national and economic security as we become even more reliant on cyber-based technology in every aspect of our daily lives.
Funding: Camps are free and funding is provided jointly by the National Security Agency and the National Science Foundation.
For more information about the national GenCyber program please visit: https://public.cyber.mil/gencyber/

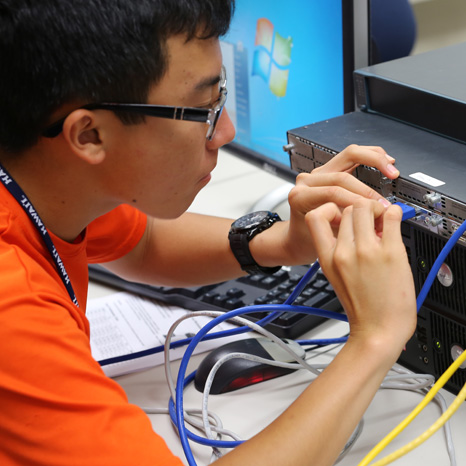
What to Expect
Campers will learn the basics of information technology and cybersecurity in a fun and comfortable setting. There will be lessons and lots of hands-on labs!
GenCyber Program Outcomes:
- An understanding of the GenCyber Cybersecurity Concepts
- Understanding and promoting ethical behavior and cyber safety
- Basic knowledge of cybersecurity terminology, concepts, tools and techniques, and
- Exposure to post-secondary educational opportunities and career pathways
Camp Topics (may be subject to change):
- GenCyber Overview
- Introduction to Cybersecurity
- Introduction to Online Safety and Ethics
- Introduction to Micro:bit with Block Coding
- Introduction to Cryptography
- Introduction to Python Programming
- Introduction to the Internet of Things
- Introduction to Electronics
GenCyber Concepts
Availability
The property that information or information systems are accessible and usable upon demand.
Confidentiality
The property that information is not disclosed to individuals, devices, or processes unless they have been authorized to access the information.
Defense in Depth
A comprehensive strategy of including multiple layers of security within a system so that if one layer fails, another layer of security is already in place to stop the attack/unauthorized access.
Integrity
The property that information, an information system, or a component of a system has not been modified or destroyed in an unauthorized manner.
Keep It Simple
The strategy of designing information and security systems to be configured and operated as simply as possible; all systems perform best when they have simple designs rather than complex ones.
Think Like an Adversary
The strategy of putting yourself inside the mindset of a potential attacker that allows you to anticipate attack strategies and defend your systems accordingly.
